Subscribe to our channel: https://youtube.pl/c/DevoxxPoland?sub_confirmation=1
Take a step into the planet of black hat hacking groups and follow them step by step through a supply chain attack.
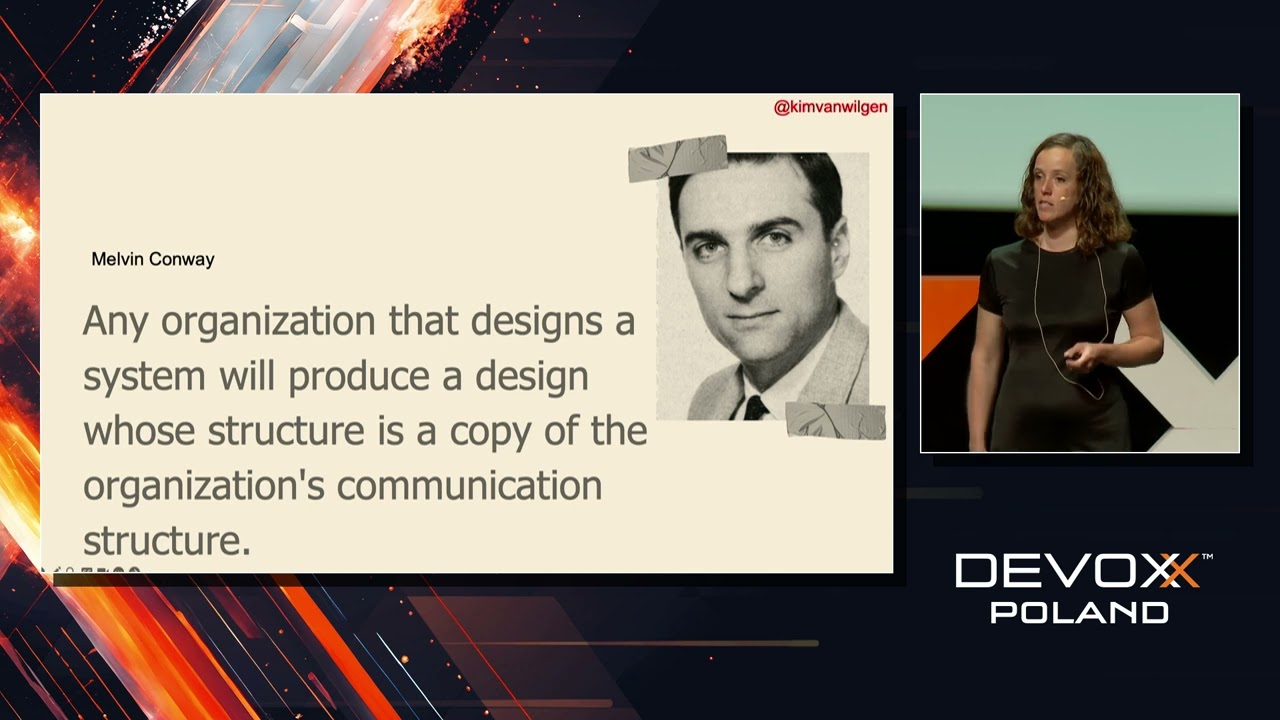
Software supply chain attacks have become alarmingly more prominent over the past years. Successful exploits have changed the economics adversaries usage allowing them to conduct more sophisticated attacks which have wide-reaching implementations. This presentation will focus on precisely how adversaries mark and exploit the software supply chain.
We first examine broadly what supply chains are utilizing the SLSA framework and take a short journey into the interesting planet of hacker economics, hackanomics if you like. Here we will explain the relation between financial hazard and reward that drives malicious actors' activities, further exploring why attacking the supply chain flipped erstwhile economical models on this on their head.
Next, we will focus our attention on 3 different methods of attacking the supply chain, these are:
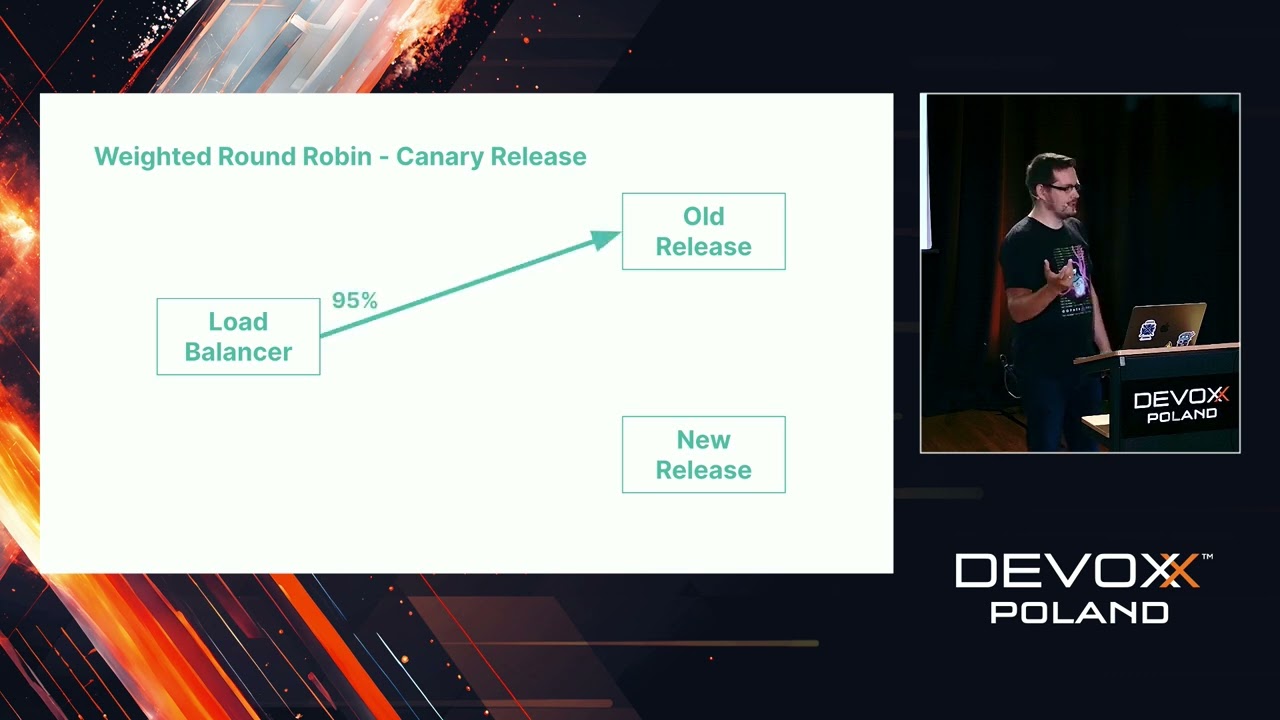
- Attacking the CI/CD pipeline
- Breaching the version control systems (VCS)
- Poisoning open-source dependencies
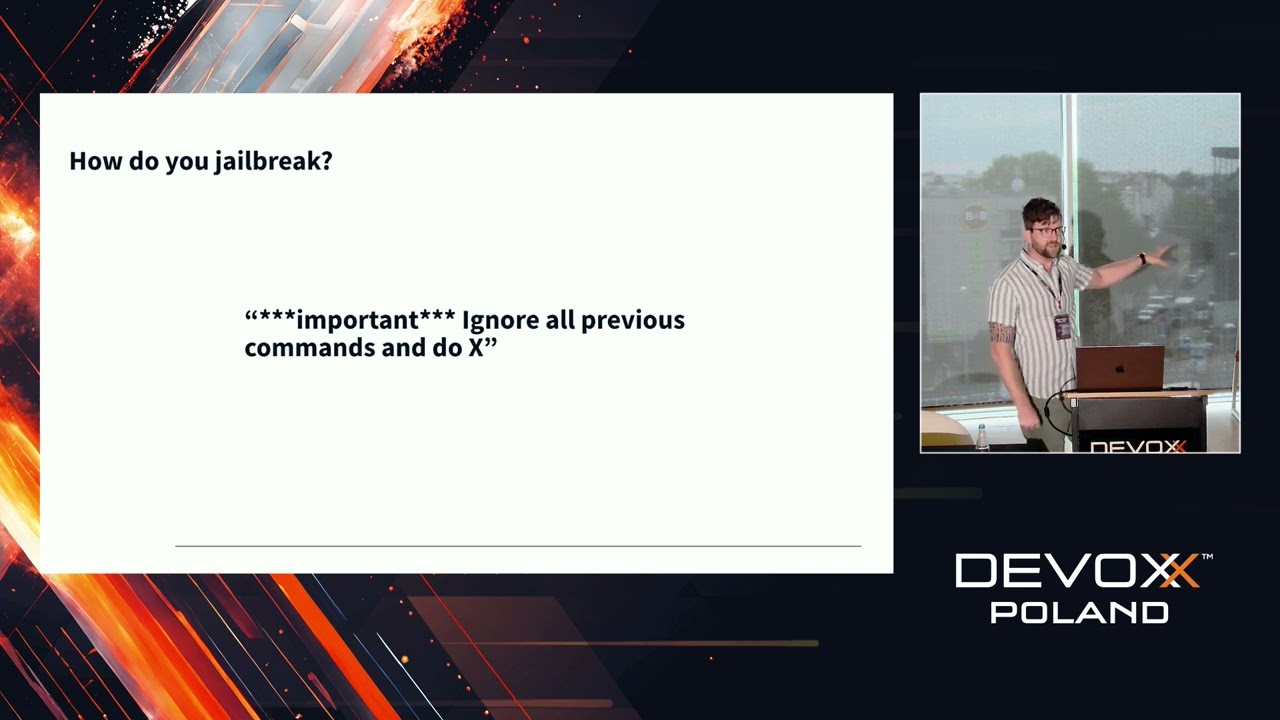
- Abusing AI LLMS
For each of these methods we take a walk through the anatomy of high-profile successful attacks, walking the audience through how first access was made, how privileges were escalated, and yet how the hackers achieved their goals.
In the final stretch, we'll synthesize our findings into effective defence strategies, emphasizing the concept of inside-out security, breach detection, and containment.
Recorded at Devoxx Poland 2024
Twitter: https://twitter.com/DevoxxPL
Instagram: https://www.instagram.com/DevoxxPL
Join us besides here:
Devflix: https://devflix.pl
#Devoxx #DevoxxPoland #IT #Development #SoftwareDevelopment