For any days now I have been dedicating any time to monitoring the 6.8-7.1 MHz band where it is possible to receive respective STANAG-4538 (3G-HF) signals and among which besides WHARQ wideband activity [1], the second waveforms developed by Harris (now:L3Harris) [1]. Figure 1 is an example.
 |
| Fig. 1 - L3Harris WHARQ traffic [1] |
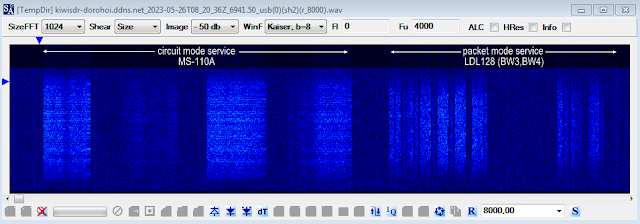 |
| Fig. 2 - STANAG-4538 traffic utilizing circuit mode and packet mode services |
After demodulation of any MS-110A segments, the presence of the well-known sync sequence:
1E 56 1E 56 1E 56 1E 00 1A 5D 1A 5D 1A 5D 1A 5D
in all the segments indicates that the traffic is secured by the Harris Citadel cryptographic engine [2], so far nothing fresh (Figure 3).
 |
| Fig. 3 |
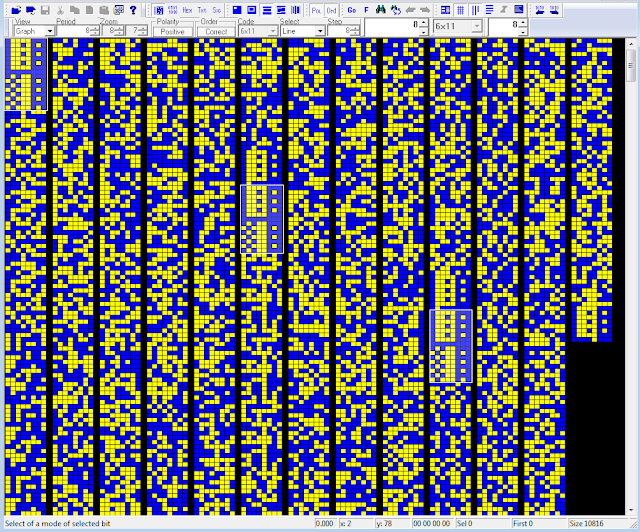
What truly amazed me is that erstwhile removed the sync series (or reshaping the bitstream to to 128-bit dimension period) a 256-bit pattern, divided in 2 parts each 3 times repeated, appear from the bitstreams... never seen before in specified secured transmissions!
74 04 9F 5C 72 1C 0F 51 CB EE 30 AA F6 01 ED 1A 54 F0 CE C2 DA 02 C8 CB 81 91 3C 8A C9 07 67 01
EE 82 FB 12 56 78 A1 2E 75 7F 21 39 26 24 A7 A8 F4 A6 CF CE 56 B0 E4 18 22 E2 F1 C0 1E 8E 17 DA
40 36 4B A6 74 6A 63 05 A5 E8 81 14 A7 65 25 73 43 26 17 13 0D AB 4C F0 90 8D 5B 5A AB A5 4C 9A
 |
| Fig. 4 - 256-bit patterns (2x128) |
Even more interesting is the fact that the bitstream resulting from the demodulation of 1 of the BW3 bursts (the same 111-byte packet was sent respective times) while indicating Citadel encryption does not show those 2x128 bits patterns (Figure 5).
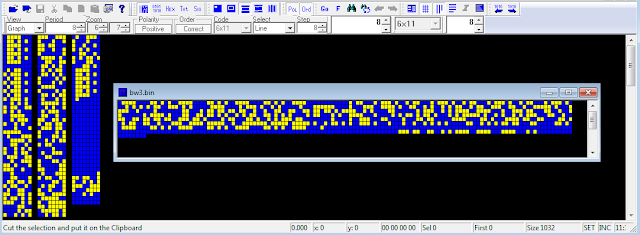 |
| Fig. 5 - BW3 bitstream (8/128 bits period) |
So:
* since, for example, KG-84/KIV-7 usage a 16 bytes dimension Initialization Vector and it is sent in 2 parts of 64 bits dimension (each 4 times repeated),
* given the presence of the well-known Citadel start/stop sequences,
* it's not an AES algorithm since the dimension of its Initialization Vector is 16 bytes regardless of the key size (12 bytes for AES-GCM)
It's a mine guess that possibly we see 32 bytes Initialization Vectors, which are sent in 2 parts of 128 bits length, each 3 times repeated, and that these transmissions could be secured by the 256-bit Harris Citadel II algorithm [3] which likely needs specified IVs.
Obviously that's just a my speculation, comments are welcome.
Monitoring was possible thanks to KiwiSDRs from Romania (YO8SGV - Dorohoi) and Russia (radiorubka - Tambov) so they must be utilizing low power and NVIS techniques.
https://disk.yandex.com/d/B_dK5qiBJTnn3g
[1] https://i56578-swl.blogspot.com/search/label/WHARQ
[2] https://www.cryptomuseum.com/crypto/harris/citadel/index.htm
[3] https://www.cryptomuseum.com/crypto/harris/citadel2/index.htm













