Nowoczesny druk w MŚP – Od kosztu do strategicznego narzędzia pracy

Fizyczny backdoor w bankomatach – atak grupy UNC2891 dzięki RaspberryPI

Czyszczą bankowe konta i zaciągają kredyty. Ten superprzekręt jest teraz na topie

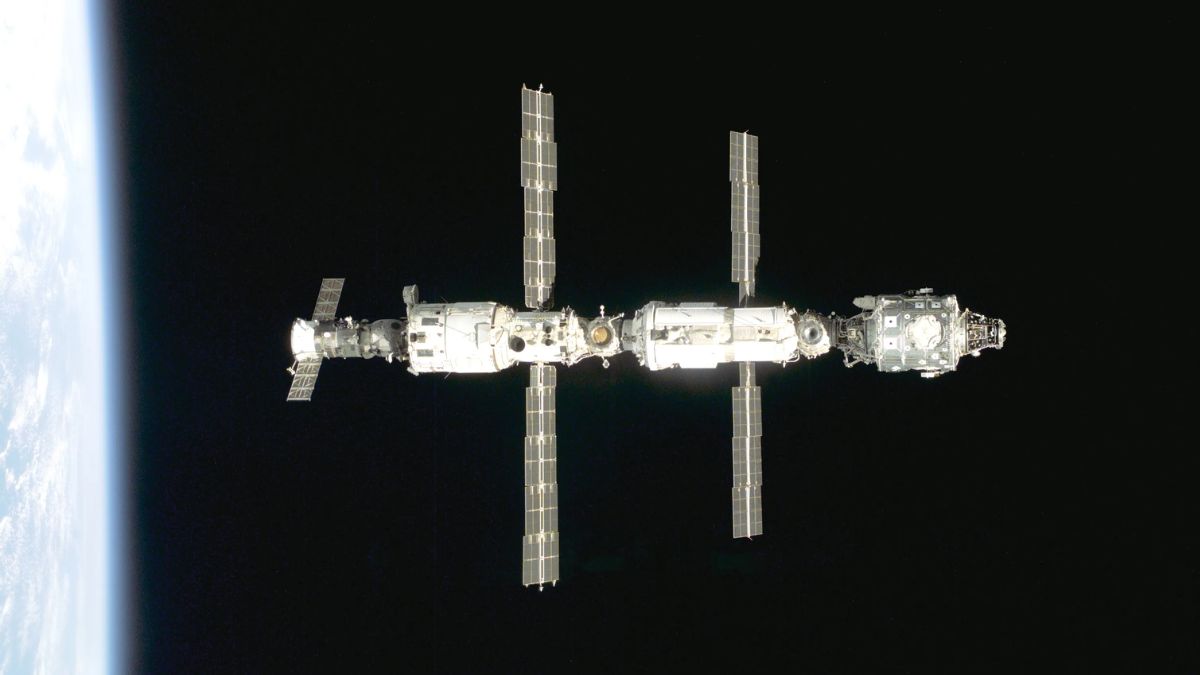
Stacja kosmiczna traci powietrze. Rosyjski moduł do wymiany
Arduino 95: Zegar z Frankfurtu, czyli jak okiełznać DCF77

Przyłóż kartę do telefonu – i po pieniądzach. Nowy sposób na oszustwo

Wyciek danych sympatyków partii Sławomira Mentzena Nowa Nadzieja

Dotacje dla firm z sektora cyberbezpieczeństwa – choćby 60 tys. euro dla MŚP

MObywatel zmienił się nie do poznania. Jak zaktualizować aplikację?
Test odporności menadżerów haseł na kradzież informacji przez tzw. infostealery
